A Guide to the Security of Web and Mobile Applications
#Tech Label November 6th, 2020It is essential to search for safety vulnerabilities in your apps as threats grow more substantial and prevalent. Application security is a way of designing, integrating, and testing security features inside applications to avoid risks such as unauthorized access and alteration of security vulnerabilities. Since 2005 there have been 1.6 billion infringements and more than 1 billion infringements since 2018. More than 31 per cent of the new victims fall under social engineering, credit card fraud, and other malicious practices every two seconds. They become victims of identity theft. This article discusses how security checks can be applied and performed securely and economically for web and mobile applications. The article also helps you manage the various types of available AST tools and advice on how and when to use each tool class.
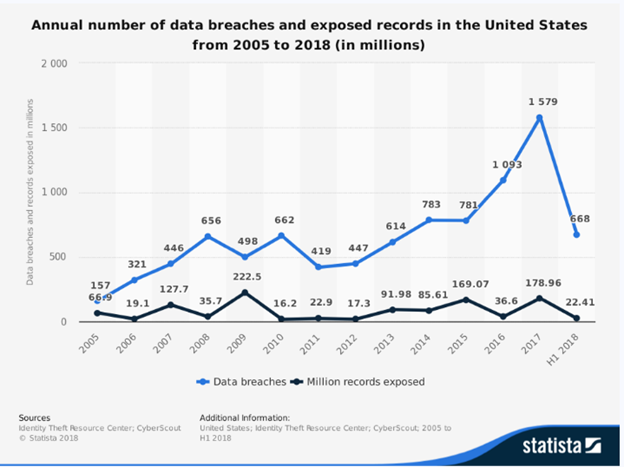
Screenshot 1: Annual data breaches
Defining the Application security
Application security is the way apps are made safer by identifying, repairing, and improving software safety. It includes security considerations in the creation and design of apps and frameworks and approaches to secure apps after deployment.
It can be said that mobile app protection is a measure to protect apps from external threats, including malware and other digital frauds that threaten sensitive personal and financial information from hackers. Mobile app security has become equally critical in today’s world. Infringements of mobile security can not only provide hackers with access in real-time to personal life. Still, they can also reveal data such as their present location, financial details, personal data, etc. Air Canada was a victim of a data infringement affecting 20,000 users in mobile apps last year. In this case, an intruder had access to passport numbers, insurance details, and more to all personal information. The business was luckily able to secure customers’ credit card information.

Screenshot 2: Mobile Security Statistics
Types of application software
Word processing software: Tools for the development of word sheets and documents form, etc. Like Microsoft Word, WordPad, etc.
Application Suites: a series of associated software packages offered. Examples: OpenOffice, Microsoft Office.
Spreadsheet software: Quantitative data estimation software. Examples: Apple Numbers, Microsoft Excel, and Quattro Pro.
Communication Software: tools for linking systems and communication in text, audio, and video. Examples: MS NetMeeting, IRC, ICQ.
Internet Browsers: Used for website connection and display. Examples
Database Software: It is used to store and sort data. Examples: Oracle, MS Access, and FileMaker Pro.
Multimedia software: Audio, video, picture, and text content mixing tools. Examples: Real Player, Media Player
Email Programs: Emailing tools.
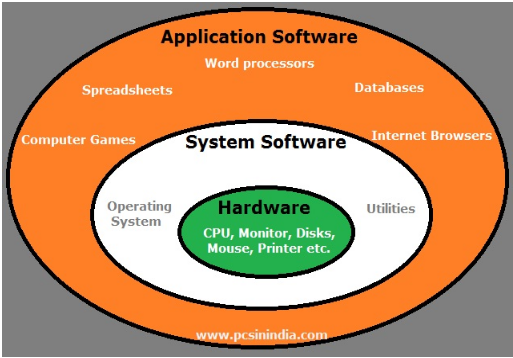
Screenshot 3: Types of app software
Mobile Application Security Checklist
We have built this extensive list of standard safety checks for mobile applications that you can use to reduce the number of vulnerabilities in your application:
- Open-source or third-party library review
- SSL / TLS security layer implementation
- Data Cache Optimization
- Local storage data security
- Client-Side Injection Prevention
- Deploy anti-tamping techniques
- Remote data Wipe and Device Lock
- Native application protection
- Implement the Least Privilege Principle
- OAuth 2.0 authorization
Common security vulnerabilities in web and mobile applications
Web app vulnerabilities
Cross-site scripting (XSS)
Cross-site scripting (XSS) targets an application’s users by inserting code into a web application output. It is typically a client-side script such as JavaScript. XSS is designed to exploit a web application’s client-side scripts to run in the manner the attacker wishes. XSS helps attackers perform hands in their browsers, steal user sessions, default websites, or redirect the user to malicious websites.
SQL injection
SQL injection is a flaw in which an attacker tries to access or corrupt database information with application code. It allows the intruder in the back-end database to build, read, edit, modify, and delete any stored data. SQL is one of the most common types of security vulnerabilities in web applications.
Cross-Site Request Forgery (CSRF
Cross-Site Request Forgery (CSRF) is an attack where a user is fooled to do an action that they have not intended to do. A third party website will submit a request for a web application that a user has already authenticated. The intruder will then use the established browser to access the features of the victim. Objectives include web applications such as social media, email users, online banking, and network interfaces.
Insecure direct object reference
Insecure direct object reference occurs when a web application exposes an internal object to the implementation. Interior items for performance include files, documents, directory, and database keys. If an application shows a URL referral to one of these objects, hackers may exploit it to access the user’s data.
Unvalidated Redirects and Forwards
There are few approaches used for redirecting and forwarding users to other sites for a particular reason. If the validation does not occur during redirections, attackers may refer victims to phishing or malware sites or unauthorized websites. An assailant may give the user a URL with a genuine URL with a malicious encoded URL. A user will search it and become a target when he sees the real part of the attacker sent URL.
Failure to restrict URL Access
Privileged websites, forums, and tools for privileged users are not presented in most applications. An attacker can access privilege pages utilizing an intelligent guess. An attacker can access sensitive pages, call up features, and display privacy. Using this vulnerability, attackers can gain access and take advantage of unauthorized URLs’ exposure without logging in. An attacker can access sensitive pages, call up features, and display privacy.
Insecure Cryptographic Storage
Insecure cryptographic storage is a common risk if confidential information is not safely stored. On websites, sensitive data include user credentials, profile information, health details, credit card details, etc. This information is saved in the database of the application. If these data are stored inappropriately by encryption or hacking, the attackers are vulnerable. An attacker may steal; change such vulnerabilities to commit identity theft, credit card fraud, or other crimes by using this vulnerability.
Security Misconfiguration
The security configuration must be specified and deployed for the application, frameworks, application server, web server, database server, and platform. An intruder can have unauthorized access to sensitive data or features if they are not configured correctly. Often such defects cause complete damage to the device. Also, keeping the program up to date is adequate protection. The attacker can list underlying information about technology and application server edition, database information, and collect information on the application to mount a few more assaults using this vulnerability.
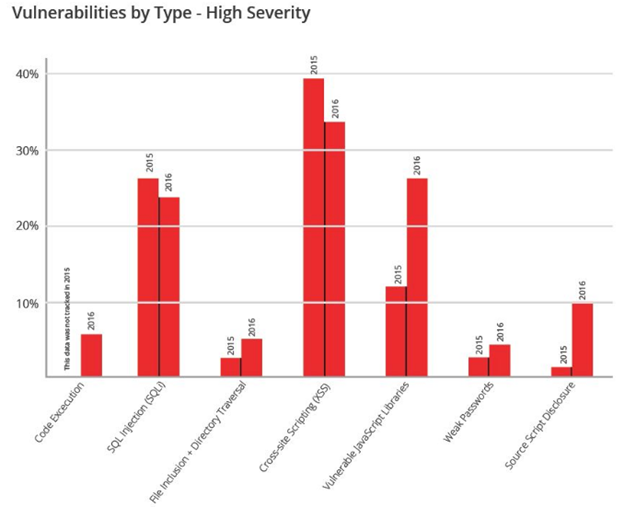
Screenshot 4: types of web app vulnerabilities
Mobile app vulnerabilities
Unintended data leakage
Many financial applications share resources with other mobile apps. As a result, user data is visible to other apps on the system.
Weak encryption
An enormous number of financial institutions either use or misemployment a strong cipher using the MD5 encryption algorithm. It makes confidential data easy to decrypt, which threats can be stolen or exploited by actors.
Lack of binary protections
Binary protection is similar to binary hardening or hardening. It makes it difficult to modify or reverse engineer a finished program. For example, the source code hiding is a way to improve an app’s safety. unfortunately, the study found that all of the financial institution applications they evaluated were unsafe to apply, encouraging the decompilation, discovering its vulnerabilities, and generating an attack by threat actors.
Execution of activities using root
Like a program manager, who can monitor what he can do on the system, offenders also have similar app rights when compromised. High privileges will give everybody the right to manipulate the standard data and settings limited to regular users.
Private Key exposure
Some apps have hard-coded API keys and private certificates either in their code or in one or more of their component files. Since these can be obtained easily due to the app’s lack of binary security, attackers could steal and use them to break encrypted sessions and confidential data, such as login credentials.
Tools for the app testing and security
Static Application Security Testing (SAST)
SAST tools may be considered as “white-hats” or “white-box tests,” in which the tester knows details about a tested device or program, like an architecture diagram, source code access, etc. To find and report bugs, SAST tools review source code that can lead to security vulnerabilities. To detect defects such as numerical errors, input validation, race conditions, path crossings, pointers, and references, the source code analyzers could be used to run a non-composed code. On the built and compiled code, the binary and byte code analyzers do the same. Some tools run only with source code, some with only compiled code, and some with each other.
Dynamic Application Security Testing (DAST)
Unlike SAST, this is a black-hat research approach where a testing tester does not know the applications it checks and seeks to detect security issues based on running application responses. For injections, device problems, user sessions, etc. DAST is used. It includes flapping and unanticipated commands to find infringements based on the load actions of the app.
Application Security Testing as a Service (ASTaaS)
As the name suggests, you pay someone with ASTaaS to test your application for protection. The service usually consists of a mixture of static and Dynamic Analytics, Penetration Testing, APIs, Risk Assessment, and more. ASTaaS can be used on conventional applications, particularly mobile and web apps.
Application Security Testing Orchestration (ASTO)
The definition of ASTO is to handle all the different AST resources in an environment in a central, organized manner and reporting. It is too early to know if the term and line of products last, but as automated testing is becoming more omnipresent, ASTO fulfills a necessity.
Origin Analysis/Software Composition Analysis (SCA)
Manual inspection-dependent information management systems are likely to fail. SCA software explores the root of all software modules and libraries. These tools help identify and identify vulnerabilities in popular and standard components, primarily open-source components. However, they do not detect in-house component vulnerabilities.
Database Security Scanning
Database-security-scanning tools Check for new versions, poor passwords, configuration bugs, ACL problems, and more. Some instruments can mine logs for patterns or acts that are unusual, including excessive administration. Generally, database scanners operate on the remaining static data while the database management system is in operation. Some scanners can track transit data.
Interactive Application Security Testing (IAST) and Hybrid Tools
Standard DAST and SAST tools can be too repetitive as they can only work with pre-configured test cases for dynamic DevOp-based agile development. It led to developing hybrid IAST tools that run dynamic application testing and create new ones with the output in previous test cases.
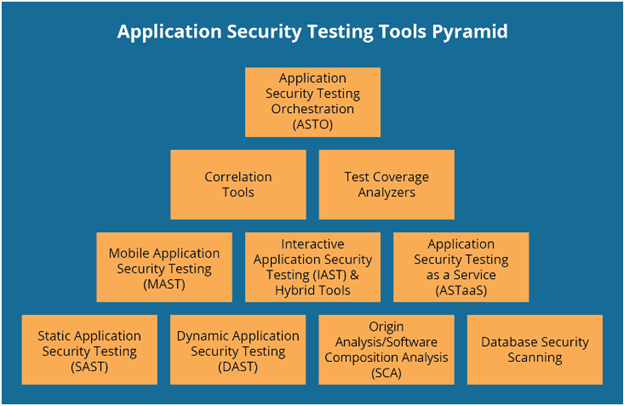
Screenshot 5: Mobile and web application security tools
Mobile Application Security Testing (MAST) Mobile and Web App Security Best Practices
Mobile app protection is maintained by the best practices that ensure the app is secure and does not divulge its personal data.
Minimal Application Permissions
Authorization enables applications to work more efficiently and freely. But they also make applications vulnerable to attacks by hackers. No application should be requested for approval beyond its operating range. Developers should stop recycling their existing libraries but create new ones that ask permission selectively.
Penetration Testing
Following infrastructural or operational upgrades, security measures can become ineffective very quickly. Periodic third-party penetration tests aid evaluate the efficiency of applied cybersecurity initiatives and respond to any incoherence. Security Monkey is a fine Netstrex tool to examine and highlight the components that need to reconfigure your AWS infrastructure.
Improved Data Security
To make sure users can easily avoid being caught up in the pit of hackers, data security policies and guidelines should be established. This can involve proper data protection as information is exchanged between devices and appropriate firewalls and security software.
Implementation of DevSecOps
The manual implementation and management of security features are sluggish, human-prone, and can be resolved based on the business’s urgency, leading to massive losses. DevSecOps or automation for secure delivery of applications is not easy. Still, it is a crucial move that enables most hazards to be mitigated and software creation and management quality to be guaranteed.
Encrypt Cache
The cache is a software component that temporarily saves the data on the computer of the user. This is used to avoid data retrieval from being delayed. If not encrypted, hackers can easily access cache data. Often, when a session finishes, the app will not erase its data, and the cache does not expire. Hackers can exploit this cache file to access user data or the server if these cache files are mistaken.
Use Third-Party Libraries with Precaution
The application development process can be streamlined, and the number of codes made by the developer reduced using third-party libraries. However, it could be a risky bid. Developers should also restrict the use of several libraries and develop a library management strategy to protect apps from attacks.
Using cloud-based security tools
There must not be modesty in the defense budgets. Many cloud providers offer PaaS security features, such as Amazon CloudTrail or the Google SteckDriver, that require not installing and running massive CAPEX systems. Your IT team will customize it and start using patented cybersecurity tools more cheaply.
Ensure HTTPS Communication
Developers must ensure that the server with which the app is linked is provided with a valid SSL certificate and only send data between the application and the server using HTTPS.
Is outsourcing web security safe?
There is an acute shortage of cybersecurity skills on the market, and it may be too expensive for the organization to collect an A-grade squad. On the other hand, managed security services companies will give you immediate access to trained professionals who provide a wide range of cybersecurity services. You have to either try to secure applications with internal resources or delegate this to a trustworthy technology provider. In any event, ensure that genuine professionals are the people you’ll be working with.
Summary
In the end, companies should understand that the impact of app safety is more significant than user safety and affects the brand’s reputation as a whole. Users are aware of the mobile app security issues and prefer apps that are secure to those that may confiscate their information with increasing hacking attempts and data violations. App developers should, therefore, try to create apps that meet the user’s needs and focus on the security aspect.
Have an upcoming project?
We're are ready to give up you a professional advice and free cost estimate.
More amazing articles to read